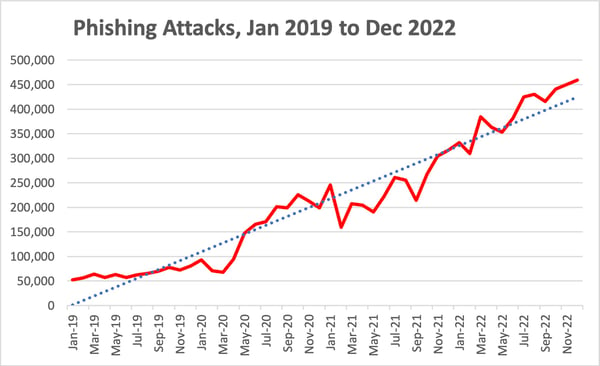
Newly Discovered Phishing Attacks Target Bank Customers
First National Bank has warned of an increase in phishing and smishing attacks, IT-Online reports.
Trish Ramdhani, head of fraud at FNB Card, stated, “In recent cases, some consumers received SMSes claiming that their bank requires them to urgently FICA by clicking on a link that takes them to the fraudster’s platform, where their information is then compromised. The technique now includes attempting to entice the user to divulge both their card information and the one-time password (OTP), which is subsequently used to complete successful transactions using smart devices.”
FNB offers the following recommendations to help people avoid falling for these scams:
- “Don’t panic: Fraudsters rely on people acting hastily due to a sense of panic. The tactics include threats that your accounts will be blocked or that fraud has been identified and must be stopped immediately. Whatever the scenario, keep in mind that such things will never compel you to give away OTPs, PINs, or passwords. It is safer to end such communication and contact your financial institution right away.
- “Do not click on email or SMS links: When opening emails from unknown sources or those that appear suspicious, proceed with caution. Clicking on links or downloading attachments from these kinds of messages should be avoided because they may include harmful malware or redirect you to fake websites.
- “Enable two-factor authentication (2FA): Enable 2FA wherever possible since it adds an extra layer of security by requiring a second verification step, which is often transmitted to your mobile device or an authenticator app, such as the FNB Apps for FNB customers.
- “Take note of the card and digital safety measures recommended by your financial institution: There is a lot of misleading information about how people may protect themselves from fraud, but it is always preferable to follow your financial institution’s recommendations on how to secure your money.
- “Keep software and devices up to date: Update your operating system, web browsers, and antivirus software on a regular basis to guard against vulnerabilities. To ensure that you get the most recent security fixes, enable automatic updates whenever possible.”






Recent Comments