Think Tanks Targeted by APT Actors
The US Cybersecurity and Infrastructure Security Agency (CISA) and the FBI have issued a joint advisory warning that nation-state advanced persistent threat (APT) actors are targeting US think tanks. The advisory says APTs are particularly interested in think tanks that focus on international affairs or national security policy.
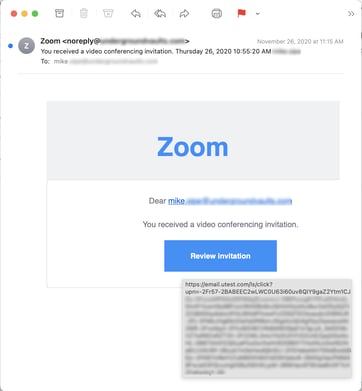
“APT actors have relied on multiple avenues for initial access,” the advisory states. “These have included low-effort capabilities such as spear phishing emails and third-party message services directed at both corporate and personal accounts, as well as exploiting vulnerable web-facing devices and remote connection capabilities. Increased telework during the COVID-19 pandemic has expanded workforce reliance on remote connectivity, affording malicious actors more opportunities to exploit those connections and to blend in with increased traffic. Attackers may leverage virtual private networks (VPNs) and other remote work tools to gain initial access or persistence on a victim’s network. When successful, these low-effort, high-reward approaches allow threat actors to steal sensitive information, acquire user credentials, and gain persistent access to victim networks.”
CISA says leaders should “Implement a training program to familiarize users with identifying social engineering techniques and phishing emails.” For employees, the advisory offers the following recommendations:
- “Log off remote connections when not in use.
- “Be vigilant against tailored spear phishing attacks targeting corporate and personal accounts
- (including both email and social media accounts).
- “Use different passwords for corporate and personal accounts.
- “Install antivirus software on personal devices to automatically scan and quarantine suspicious
- “Employ strong multi-factor authentication for personal accounts, if available.
- “Exercise caution when:
- “Opening email attachments, even if the attachment is expected and the sender appears to be known. See Using Caution with Email Attachments.
- “Using removable media (e.g., USB thumb drives, external drives, CDs).”
New-school security awareness training can help organizations of all types defend themselves against cyberattacks by enabling employees to recognize social engineering tactics.
Recent Comments